Computers and the Internet of Things gadgets are only two examples of things that can be hacked if they have an Internet connection. Today, even the tiniest gadgets collect personal data, making them a doorway for hackers to access private information on millions of individuals. If your website or web application has a database, it is sufficient justification to safeguard your website and fix any security flaws if your database contains information about your users.
A single DDoS assault, according to Corero, may cost a business upwards of $50,000 in lost revenue. Users’ personal information and, more crucially, their faith in your company are lost in the event of a security breach. Additionally, losing confidence results in much bigger monetary and reputational damages.
Best Practices for Website Security
Documenting changes in your software
Since it’s usually simpler to find anything in a space where everything is in its place, the first item on our web application security checklist doesn’t seem to be as challenging at first. However, becoming organized never has time in real life. The same is true with software: as soon as your online application is live, further features and updates are added.
Identify potential entry points for hackers
Because software and programs interact with customers and process data transactions, some components of your program are more prone to security threats than others. Divide your software’s features into modules based on security priorities to ensure that you concentrate on doing web application security tests in the proper places. Website developers in Dubai recommend that you divide your software modules into subcategories as follows:
Critical modules contain the most exposed, client-facing, and internet-connected functionalities. For hackers, they are the most alluring access points. Checkout pages and login screens are two examples.
Serious modules are modules that contain sensitive data about the firm or its consumers
Normal modules need maintenance and regular reviews even though they don’t directly access private data in your app.
Use Firewall
The purpose of a firewall is to filter out the traffic between a server and a user and analyze the queries between them to identify if there is any malicious activity passing through into the database.
The most widely used tool to secure software is Firewall since it restricts any entry points for malicious activity to pass through. They are easy to use since they do not require web developers to make changes to the code.
The only limitation for some firewalls is that they can’t detect all types of threats. This is why it’s important to invest in the best firewall since it can allow you to identify and block SQL injection attacks and cross-site scripting attacks to maximize your website security.
Encryption methods
Use fundamental tools like HSTS encryption and HTTPS but don’t stop there.
For any user information you give to the server and receive from it, utilize SSL encryption. Even if HTTPS is fantastic and almost impossible to man-in-the-middle attacks, it is insufficient if someone has access to your server.
Keep your applications and software updated
When mentioning upgrading a web application, we don’t only mean the software itself but also all the third-party services and libraries that make up the infrastructure of the application. Beware of these dangers as well, as hackers frequently utilize third-party software to compromise the primary system. Your web app’s documentation will be quite useful in this situation.
To find out which libraries you utilize, look at your documentation. Eliminate the ones that don’t genuinely improve your app, then update the rest of them. Create an update strategy, at the very least, as upgrading libraries seems simpler than it is. Since newer versions could not be backward compatible with older ones and break the entire system, many developers are hesitant to update third-party services for their software.
Penetration testing
One of the most sophisticated aspects of any security assessment is penetration testing. It places your software in nearly real-world scenarios where a QA professional assumes the role of a hacker and attempts to compromise the system using any technique, from physical harm to programming.
The majority of vulnerabilities may be successfully found through penetration testing, which also produces a thorough report that can be used as a foundation for a security check and a reference for identifying the weakness that led to a breach. To ensure that all possibilities are taken into account, penetration testing offers several ways.
Software flaws can occur for more than ten different causes, and a typical medium-complexity online program has dozens of entry points that hackers can exploit, such as cloud access. This is the purpose of penetration testing: it enables a QA to act out several scenarios and attempt to penetrate the system with the same level of expertise that a hacker would have in a real-world scenario.
Real-time Monitoring System
Even with serious security breaches, it often takes a corporation six months to discover them, according to Ponemon. If you keep a lot of sensitive data, detecting and fixing any breaches should be your priority. You may do this by using specialized monitoring software, which can find every move your employees make on company computers. This can assist you in ensuring that all security criteria are satisfied.
90% of security breaches, according to ChiefExecutive.com, are made possible by human mistakes. Since everything is documented when you monitor your staff, you can instantly determine which activity on which computer corrupted your system.
Train Your Employees
Human error, which we’ve already discussed, is more prevalent when people are unaware of the potential places for error. It’s simple to lose sight of the everyday challenges your workers face in many divisions if your company is very large.
Although you can always keep an eye on your staff, it’s more beneficial to stop a security breach before it happens than to go for the root of the problem after it has already happened. Inform your staff on how to use software safely and what behaviors might result in data infringement. Develop security guidelines that govern their behavior and teach them what to do in the event of a data breach. You must go to the following step to do that.
Always prepare for the worst
Many businesses lack a web application security plan or a response strategy in the event of a cyber security incident. This results in:
- Sluggish reaction to cyberattacks
- Significant time and financial losses
- Loss of confidence among both clients and workers
Your strategy should categorize different types of assaults and include a list of steps to do for each category, along with a deadline. You should not only have an emergency plan but also test it frequently to ensure that your systems are functional and your staff can respond appropriately.
Monitor your permissions
Limit access to your software according to employees’ needs. Create a permission-level grid to provide your employees with the permissions they need for their work.
There are two primary benefits to granting varying levels of system access to your employees. First, you’ll make sure that anyone who gains access to your system using an employee’s credentials can only go as far as the system permits.
Second, you’ll be certain that your employee can’t genuinely access all critical data through their account if they wish to place your business in a tough scenario. Another recommended practice for website security is to block ex-workers and change passwords once a developer departs an organization.
Final Suggestions
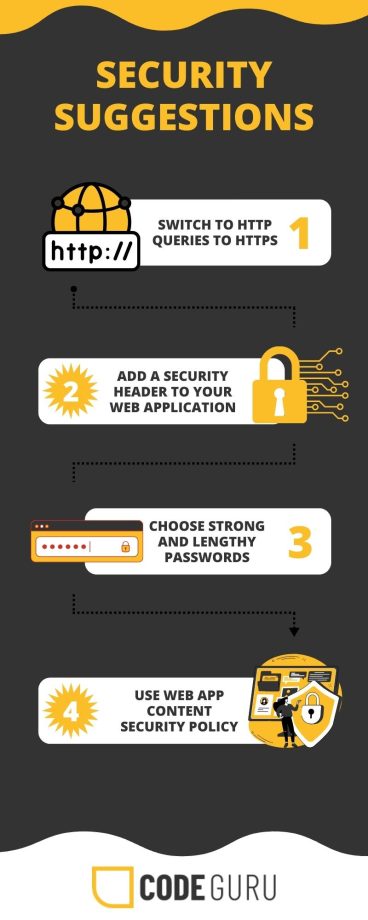
Other ideas that you might find helpful include the following:
- To switch all of your HTTP queries to HTTPS, purchase an SSL certificate or use an encryption service (like Let’s Encrypt).
- To prevent cross-site scripting, add a security header to your web app.
- Choose secure passwords since hackers typically choose basic, short, and recognizable passwords to access your system.
- Using a web app content security policy, specify the sources of authorized material. This will stop any files from being loaded onto your website from a potentially harmful source.
Final Thoughts
Through this article, I have explained in detail the 10 best website security practices to stay safe from cyber attacks. Although this may not guarantee that you don’t won’t get attacked, it does reduce the chances of it happening significantly.
To maintain this level of security you need to ensure that you document all the changes and make sure all third-party libraries and frameworks are kept up to date. It’s also crucial to try penetration testing to try and compare how well your security is while facing real-life scenarios of possible threats. And lastly as mentioned above, always train your employees to be aware of the possible threats that they may encounter and how to effectively work against them.
If you feel like maintaining a strong and secure web application but don’t have all the knowledge about it, you can always reach out to us and we can guide you and create your website as per your needs.
FAQs
What are the most common web app security vulnerabilities?
The most typical methods for a hacker to access your online application are as follows:
- Faults in injection
- Authentication problems
- Exposed sensitive data
- A security configuration error
- XSS: cross-site scripting
- Direct object references that are not safe
- Fake cross-site requests
- Using vulnerable third-party components
- Unverified forwards and redirects
How do I protect myself from cyber-attacks?
To protect yourself from cyber-attacks you need to first create a website security strategy. When developing a website, at each stage of development security checks should be done to reduce the risks of a security breakthrough. Also, it’s crucial to use only trustworthy third-party services in web applications and make sure they are constantly updated.
How do you remove malware after you are infected?
You need to download antivirus software and run a scan on your computer to let it identify any malware on your computer. Once the antivirus software assesses your infection level it will then proceed to remove them.
Another way to remove the malware is by removing it manually however, this is very hard to do even for experienced computer users. Antivirus software would be the best at removing them.
How does malware find me?
Even if you take precautions, using the Internet often might expose you to viruses. Here are a few ways you might get exposed to a virus
Any media-supported website you visit will undoubtedly set a tracking cookie.
Exchange data, music, or pictures with other people.
Install software without reading licensing agreements in their entirety.
What should I look for in anti-malware software?
- Regularly updated definitions
- Highly accurate malware detection
- Proactive defense
- Specialized threat research group
- Customer Assistance
- User-friendly interface
- Dependable business to support the software